How to Install ModSecurity for Apache2 on Ubuntu 18.04
Requirements
- AWS Account. Create your own AWS Account
- Amazon EC2 Ubuntu 18.04. Learn how to deploy Ubuntu 18.04 on AWS
- A user with sudo privilege command.
To get started, This guide shows you step process on how to install ModSecurity for Apache2 on Ubuntu 18.04 within Amazon EC2 instance.
Step 1. Install Apache2 Web Server
SSH remote into your Ubuntu server using your favorite terminal console. Below, you need to install an Apache2 web server for you to enable the Modsecurity module and configuring the security rules set.
sudo add-apt-repository ppa:ondrej/apache2 sudo apt update sudo apt-get install apache2 -y
See: Learn how to install Apache2 Web Server on EC2 Ubuntu 18.04
We assume that you have already installed Apache2 Web Server in your Ubuntu server.
Step 2. Install Modsecurity
To install modsecurity on EC2 Ubuntu instance, run the command:
sudo apt-get install libapache2-mod-security2
After installation completes, restart the Apache2 service.
sudo service apache2 restart
Now verify the modsecurity module if properly installed on your environment, run the command:
sudo apachectl -M | grep security
The output should be the same as below:
security2_module (shared)
Step 3. Configure Modsecurity
After installing Modsecurity, there is a default configuration file that you need to enable and configure. Run the command:
sudo cp /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
Modify the file that you have copied using the vim editor.
sudo vim /etc/modsecurity/modsecurity.conf
Find for SecRuleEngine DetectionOnly and replace with SecRuleEngine On.
# SecRuleEngine DetectionOnly SecRuleEngine On
Save and close the file.
Restart the Apache2 service to effect the changes.
sudo service apache2 restart
Step 4. Setup Rules for Modsecurity
ModSecurity has default rules set located at /usr/share/modsecurity-crs directory. Well, do not recognize these rules as we need to download the recommended latest version from Coreruleset.org
Create a new folder under the Apache directory, use the command:
sudo mkdir /etc/apache2/modsecurity.d
Now, download the Modsecurity core rule set from Github using:
sudo git clone https://github.com/coreruleset/coreruleset.git /etc/apache2/modsecurity.d/owasp-modsecurity-crs
After downloads completed, open the modsecurity folder under apache2 directory.
cd /etc/apache2/modsecurity.d/owasp-modsecurity-crs
Next, copy the sample configuration file from the downloaded rules set, type command:
sudo cp crs-setup.conf.example crs-setup.conf
Edit the Apache2 configuration file using:
sudo vim /etc/apache2/apache2.conf
Add the lines below:
| <IfModule security2_module> | |
| Include modsecurity.d/owasp-modsecurity-crs/crs-setup.conf | |
| Include modsecurity.d/owasp-modsecurity-crs/rules/*.conf | |
| </IfModule> |
Save and close the file.
Next, open the file at /etc/apache2/mods-available/security2.conf and comment the line:
# IncludeOptional /usr/share/modsecurity-crs/owasp-crs.load
Save and close the file.
Next, verify your Apache2 configuration using:
sudo apache2ctl configtest
If all goes well, begin to restart your Apache2 service.
sudo service apache2 restart
Make sure to check your website to see if it’s still running properly.
Step 5. Testing Modsecurity
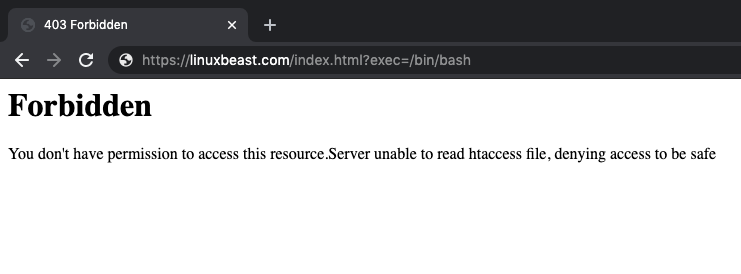
You can now try to execute a malicious URL in a browser or terminal console and see if the ModSecurity rules are triggered.
Browser
https://linuxbeast.com/index.html?exec=/bin/bash
After running the URL on the browser, you should get a Forbidden error message like this:
Terminal Console
curl -I https://linuxbeast.com/index.html?exec=/bin/bash
After running command in the terminal console, this would be the forbidden error message looks like:

To learn more about Modsecurity:
See: https://github.com/SpiderLabs/ModSecurity/wiki/Reference-Manual-(v2.x)
Extra Tips
If you want to excludes directories or removing rules set from match URI, use the guides below:
Execution error – PCRE limits exceeded (Error)
Solutions: Increase the limits
SecPcreMatchLimit 500000 SecPcreMatchLimitRecursion 500000
Modify this file:
sudo vim /etc/modsecurity/modsecurity.conf
See: https://github.com/SpiderLabs/owasp-modsecurity-crs/issues/656#issuecomment-262780221
MULTIPART_UNMATCHED_BOUNDARY (Error)
Solution: Modify SecRule
From:
SecRule MULTIPART_UNMATCHED_BOUNDARY "!@eq 0" \ "id:'200004',phase:2,t:none,log,deny,msg:'Multipart parser detected a possible unmatched boundary.'"
To:
SecRule MULTIPART_UNMATCHED_BOUNDARY "!@eq 0" \ "id:'200004',phase:2,t:none,nolog,allow,msg:'Multipart parser detected a possible unmatched boundary.'"
Disable/Enable ModSecurity Per Directory
<Directory /usr/share/phpmyadmin>
SecRuleEngine Off
</Directory>
<Directory /var/www/wordpress>
SecRuleEngine On
</Directory>
Removing Rules Set from WordPress match URI
| <VirtualHost *:80> | |
| <LocationMatch “/wp-admin”> | |
| SecRuleRemoveById 950109 950901 950117 958030 960024 970903 973300 973301 973304 973332 973333 973338 981143 981172 981173 981245 950007 950120 981231 | |
| </LocationMatch> | |
| <LocationMatch “/wp-admin/nav-menus.php”> | |
| SecRuleRemoveById 960335 | |
| </LocationMatch> | |
| <LocationMatch “/wp-login.php”> | |
| SecRuleRemoveById 950007 950109 950117 950120 950901 981143 981172 981173 970901 970903 | |
| </LocationMatch> | |
| <LocationMatch “/wp-content”> | |
| SecRuleRemoveById 950007 950120 958231 970903 981172 | |
| </LocationMatch> | |
| <LocationMatch “(/wp-admin/options.php|/wp-admin/theme-editor.php|/wp-content/plugins/)”> | |
| SecRuleRemoveById 950005 950006 950907 958009 959006 959070 960008 960011 960904 973334 973335 973344 973347 981231 981317 | |
| SecRuleRemoveById phpids-17 # Detects JavaScript object properties and methods | |
| SecRuleRemoveById phpids-20 # Detects JavaScript language constructs | |
| SecRuleRemoveById phpids-21 # Detects very basic XSS probings | |
| SecRuleRemoveById phpids-30 # Detects common XSS concatenation patterns 1/2 | |
| SecRuleRemoveById phpids-61 # Detects url injections and RFE attempts | |
| </LocationMatch> | |
| <LocationMatch “/wp-admin/options-general.php”> | |
| SecRuleRemoveById 960335 | |
| </LocationMatch> | |
| <LocationMatch “/wp-includes”> | |
| SecRuleRemoveById 950006 950007 950120 959006 960010 960012 970903 981172 | |
| SecRuleRemoveById phpids-17 # Detects JavaScript object properties and methods | |
| SecRuleRemoveById phpids-20 # Detects JavaScript language constructs | |
| SecRuleRemoveById phpids-21 # Detects very basic XSS probings | |
| SecRuleRemoveById phpids-30 # Detects common XSS concatenation patterns 1/2 | |
| SecRuleRemoveById phpids-61 # Detects url injections and RFE attempts | |
| </LocationMatch> | |
| <LocationMatch “/wp-admin/post.php|/wp-admin/edit.php”> | |
| SecRuleRemoveById 980140 950001 950007 950120 958977 959070 959072 959073 960335 970901 973306 973316 973334 973335 973343 973344 973347 981231 981243 981244 981246 981249 981257 981318 970903 981172 981256 | |
| </LocationMatch> | |
| <LocationMatch “/wp-admin/admin-ajax.php”> | |
| SecRuleRemoveById 950911 970901 973306 973316 973334 973335 973344 973347 981231 981257 981318 970903 950007 950120 981172 981242 981244 2100081 | |
| </LocationMatch> | |
| <LocationMatch “/wp-admin/async-upload.php|/wp-admin/media-new.php”> | |
| SecRuleRemoveById 200004 | |
| </LocationMatch> | |
| <LocationMatch “/favicon.ico”> | |
| SecRuleRemoveById 950007 950120 981172 981243 970903 | |
| </LocationMatch> | |
| <LocationMatch “/feed”> | |
| SecRuleRemoveById 970901 | |
| </LocationMatch> | |
| <LocationMatch “/xmlrpc.php”> | |
| SecRuleRemoveById 950001 959070 959071 959073 973302 973332 973333 973334 973335 973344 973347 981244 981248 981249 981256 981317 981320 | |
| </LocationMatch> | |
| </VirtualHost> |